The goal is to experiment WebLogic Security for the Application level. Only particular group of user can have the access to the application. To achieve this we need to create the users and groups in the Security Realm. In real time systems there could be hundreds of users and many groups which can be configured through nice GUI and Authentication Provider third party tools.
Experiment Specification
To Create WebLogic Administration Security:
Step 1: Go to Domain Structure tree (here in my example RANJITH_DOMAIN) at left side and Click on Security Realms link as shown below:
Step 2: Click on myrealn as shown below:
Experiment Specification
To Create WebLogic Administration Security:
Step 1: Go to Domain Structure tree (here in my example RANJITH_DOMAIN) at left side and Click on Security Realms link as shown below:
Step 2: Click on myrealn as shown below:
Step 4: Create a new User
Users Creation like this below:
lly,we have to create another 3 users same as above
Groups Creation like below:
--> Go to Groups tab and click on New button as shown below:
--> enter the Groups details as below like this:
lly, we have to create managers group also.
Step 5.1: Navigate to Users and Groups tab -> Users -> click on user name(kiran) -> click on Groups and that user(kiran) assigned to which group belongs(employees,managers) as shown in the below:
Step 5.2 : lly,we have to do same process like above (mehar,ranjith,vidhya sagar) also.But we remember one point according to our table (ranjith,vidhya sagar) are employees .So,we
need to select employees group only.
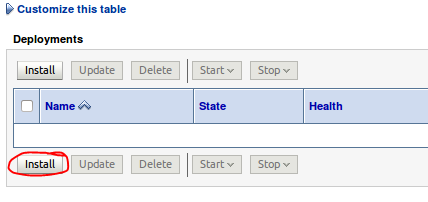
Step 6 : Download timeoff.war file .
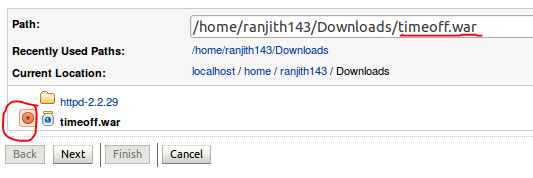
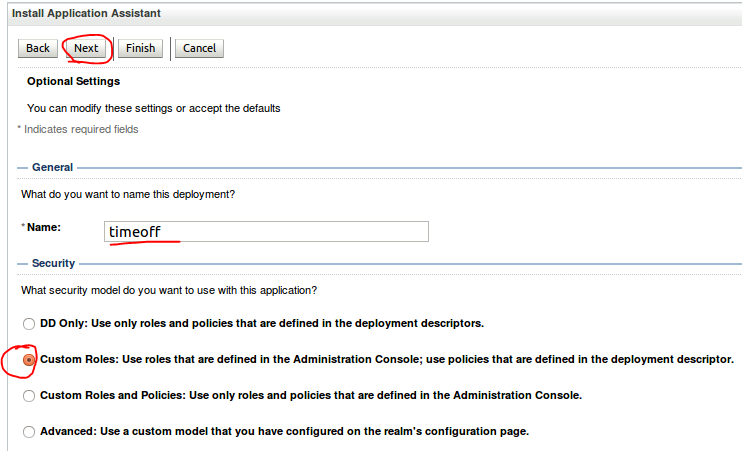
Deployment an application , again go to Deployment --> Install -->Path(where you download war file) and check radio button (timeoff.war) --> Next --> Next -->cluster1
-->Next
lly, we have to create managers group also.
Step 5.1: Navigate to Users and Groups tab -> Users -> click on user name(kiran) -> click on Groups and that user(kiran) assigned to which group belongs(employees,managers) as shown in the below:
Step 5.2 : lly,we have to do same process like above (mehar,ranjith,vidhya sagar) also.But we remember one point according to our table (ranjith,vidhya sagar) are employees .So,we
need to select employees group only.
Step 6 : Download timeoff.war file .
Deployment an application , again go to Deployment --> Install -->Path(where you download war file) and check radio button (timeoff.war) --> Next --> Next -->cluster1
-->Next
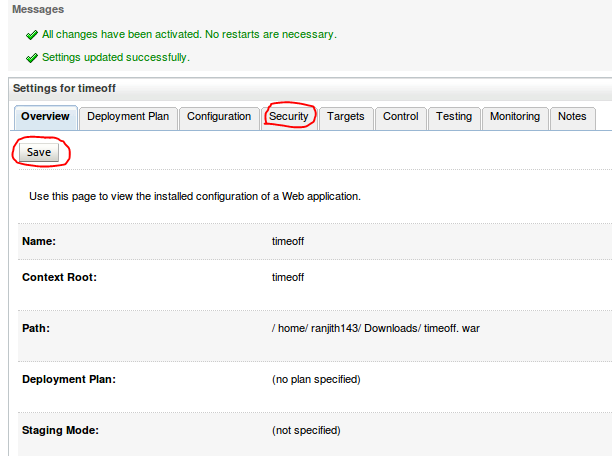
Next --> Finisth ---> Save.
Step 7 : Go to Security tab --> Url Patterns -->New ---> URL Pattern: /managers/* --> Name: director --> OK.
Step 8 : Click on director --->Add Conditions --> Predicate List : Group ---> Next ---> Group Argument Name: managers --> Add --> Finish --> Save.
Step 7 : Go to Security tab --> Url Patterns -->New ---> URL Pattern: /managers/* --> Name: director --> OK.
 |
| Add Condition to the role |
Step 9 : Again go to Deployment --> click on timeoff --> Testing
Try to access the application URL then click the link 'Close office' that will be allowed only for the managers group users that is kiran in my example. It worked!! When I try with non-manager users it is not accessible. Just see in below images to understand what happens here.......
Try to access the application URL then click the link 'Close office' that will be allowed only for the managers group users that is kiran in my example. It worked!! When I try with non-manager users it is not accessible. Just see in below images to understand what happens here.......
Step 10: Try to access the application URL then click the link 'Close office' that will be allowed only for the managers group users that is kiran ,enter kiran name and password.It will access the page. That means in groups managers can only access the this application ,not for employees or others. Just try in urs systems .............
Quiz
Quiz
Identify three options for Keystores in a server's
configuration.
A. Demo Identity and
Demo Trust
B. Demo Identity and
Java Standard Trust
C. Java Standard
Identity and Custom Trust
D. Custom Identity and
Demo Trust
E. Custom Identity and
Custom Trust
F. Custom Identity and
Command Line Trust
Here
my experiment given me clarity on this question, the answer is AEF
























No comments:
Post a Comment